Oracle E-Business Suite (EBS) customizations seem to solve immediate business needs, but they often create an invisible burden of technical debt that compounds over time. For CTOs and Technology Directors, understanding and mitigating these hidden risks is crucial for long-term system sustainability, operational efficiency, and competitive advantage.
The Growing Technical Debt Crisis in Oracle EBS

Technical debt represents the accumulated cost of choosing expedient solutions over better approaches. Research indicates that technical debt accounts for as much as 40% of IT balance sheets, with 70% of ERP transformation failures attributed to underestimating legacy complexity and technical debt.
In Oracle EBS environments, this manifests through extensive customizations that seemed reasonable at the time of implementation but now threaten system stability and future growth. The challenge is particularly acute for Oracle EBS users, where customizations have become so embedded in business operations that they’re nearly impossible to untangle. Many organizations discover that their customizations don’t follow Oracle standards during upgrade projects, creating significant remediation challenges when migrating to newer versions.
Hidden Risks That Compound Over Time
Performance Degradation and System Instability
Customizations that bypass Oracle’s standard APIs and data access methods create immediate performance risks. When organizations modify Oracle’s seeded objects directly or implement customizations without following proper development standards, they introduce instability that becomes more pronounced as transaction volumes grow.
The invasiveness of customizations directly correlates with their risk profile. Oracle categorizes customizations based on their potential to disrupt system functionality, with the most invasive modifications creating the highest risk of system failures during upgrades or routine maintenance.
Security Vulnerabilities and Compliance Gaps
Custom code often introduces security vulnerabilities that standard Oracle security controls cannot address. These vulnerabilities include SQL injection risks, inadequate access controls, and data exposure through custom interfaces without rigorous security testing.
From a compliance perspective, heavily customized Oracle EBS environments face significant challenges meeting Sarbanes-Oxley (SOX) requirements. Custom modifications can bypass built-in audit controls, creating gaps in data security and audit trails that auditors flag as material weaknesses. Organizations must implement additional audit mechanisms specifically for customized components, increasing complexity and compliance costs.
Interpreting the Oracle EBS Security Processes Matrix

To better understand how customizations impact Oracle E-Business Suite security and compliance, refer to the matrix below, which maps out the essential operational processes, Access Management, Secure Configuration, Data Protection, and Vulnerability Management, across the four core Oracle EBS system components: Application, Database, Application Server, and OS/Network.
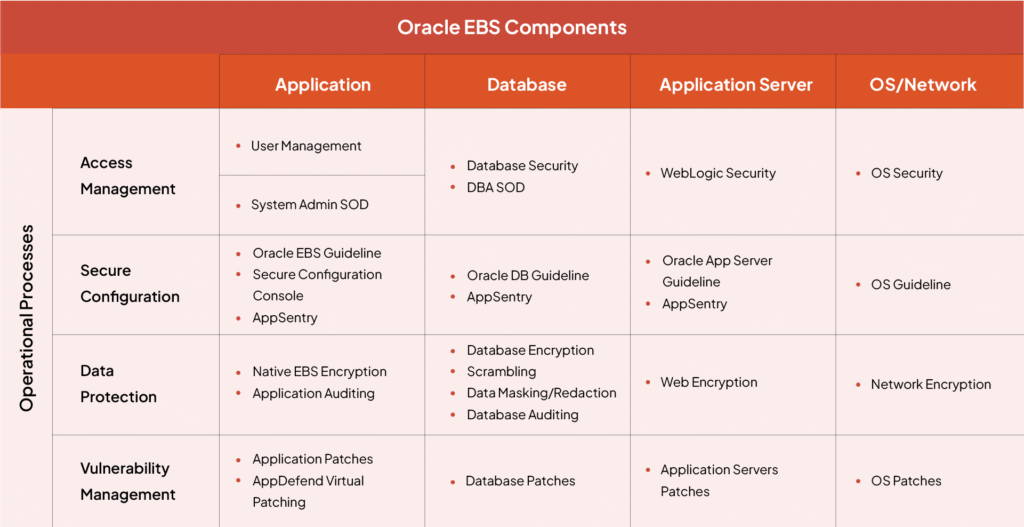
This visual framework underscores how robust security and compliance demand coordinated controls at every level of your EBS landscape. However, when custom code, extensions, or workarounds are introduced, these standard controls are at risk of being circumvented or rendered incomplete. For example:
- Access Management: Out-of-the-box user controls and segregation of duties may be sidestepped by custom user interfaces or direct database access routines. Custom logic could unintentionally elevate privileges or bypass established authentication checks.
- Secure Configuration: Oracle provides guidelines and tooling to lock down critical configurations, but customizations may ignore or override these hardening steps. This creates weak points susceptible to exploitation, especially if developers are unfamiliar with current security baselines.
- Data Protection: Standard encryption, scrambling, and auditing features safeguard sensitive information. Yet custom code can process data outside these controls, often without sufficient input validation or encryption, exposing critical business data to leaks, tampering, or unauthorized queries.
- Vulnerability Management: While Oracle delivers regular patches and security updates, customizations often complicate patch cycles or introduce unpatched code paths. These neglected areas can become prime targets for attackers, prolonging exposure well past compliance requirements.
Compliance Gaps Magnified by Customizations
Regulatory frameworks such as Sarbanes-Oxley (SOX) depend on the ability to enforce and audit controls consistently across all system layers. The matrix reveals—and real-world breaches confirm—that customizations can break this chain of trust. Audit trails may not capture activities occurring within custom code, and access logic might not support mandated separation of duties or incident response protocols. Compliance teams must deploy manual or secondary controls to monitor custom objects, driving up cost and complexity while decreasing overall assurance.
Why This Matters for Technology Leaders
This matrix serves as a strategic diagnostic tool for CTOs and technology directors. It highlights the need for routine, systematic audits of standard Oracle EBS features and every custom component, integration, and workflow. Without such proactive oversight, organizations risk accumulating undetected vulnerabilities and material compliance weaknesses that can result in regulatory penalties, reputational damage, and loss of business trust.
Upgrade and Maintenance Complexity
The 12.2 upgrade cycle has exposed the actual cost of excessive customizations. Oracle’s Application Development Online Patching (ADOP) process enforces coding standards that many legacy customizations fail to meet. Organizations face substantial CEMLI (Configurations, Extensions, Modifications, Localizations, Integrations) remediation efforts, where the technical work often outweighs functional requirements.
Common upgrade challenges include:
- Non-compliant custom objects requiring extensive modification
- Performance degradation post-upgrade due to incompatible customizations
- Extended testing cycles to validate custom functionality
- Increased downtime during upgrade implementation
Cost Escalation and Resource Drain
Maintaining extensive customizations consumes disproportionate resources. Studies show developers spend an average of 13.4 hours per week on technical debt-related activities, representing a significant portion of IT budgets devoted to non-productive maintenance. The compounding nature of technical debt means that costs increase exponentially over time if not actively managed.
Organizations with heavily customized Oracle EBS environments report:
- Higher total cost of ownership (TCO) due to ongoing maintenance requirements
- Reduced agility in responding to business process changes
- Difficulty attracting and retaining skilled developers willing to work with legacy customizations
Case Study: Global Manufacturer Cuts Technical Debt with Multi-Site Oracle EBS Upgrade

A global manufacturer of electric motors faced the hidden cost of legacy customizations during a multi-site Oracle EBS upgrade. The organization operated multiple EBS versions (11.5.10.2, 12.1.3, and 12.2.x) with years of customizations that conflicted with Oracle standards and slowed performance. The Oracle EBS upgrade to 12.2.x required:
- Comprehensive CEMLI inventory and remediation to align with supported frameworks
- Optimization or retirement of redundant custom code to enable new EBS features
- Database upgrades to Oracle 12c across all environments
- Implementation of high-availability infrastructure (RAC, ASM, DMZ) to ensure uptime
- Multi-phase testing to validate core manufacturing and supply chain processes
The project delivered a unified, high-performing EBS environment with reduced customization risk, enabling faster adoption of Oracle’s Continuous Innovation releases and better readiness for cloud integration.
Strategic Approaches to Managing Oracle EBS Technical Debt

Conduct Regular Customization Audits
Implement systematic reviews of all customizations to identify and prioritize remediation efforts. Use Oracle’s Global Standards Compliance Checker (GSCC) and Readiness Reports to identify non-compliant customizations quickly. Focus audits on:
- High-impact customizations that affect critical business processes
- Modifications that bypass Oracle’s standard APIs
- Custom code that manipulates core Oracle tables directly
- Integrations that haven’t been updated to use modern Oracle interfaces
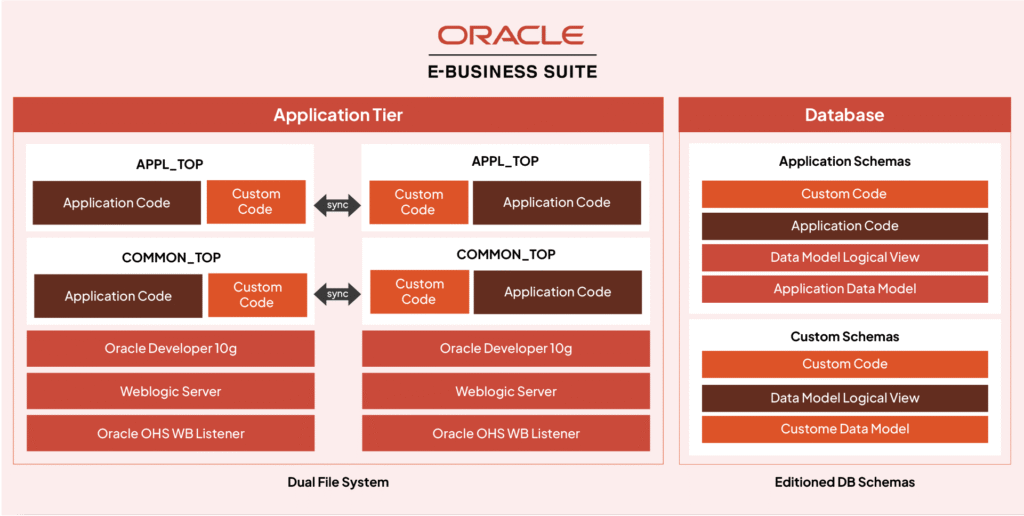
The image above provides a clear, architectural view of managing and distributing custom code across the Oracle E-Business Suite (EBS) landscape. Understanding this structure is essential for recognizing where hidden security vulnerabilities and compliance gaps can emerge.
Dual File System and Editioned DB Schemas: A Double-Edged Sword
Oracle EBS employs a dual file system on the Application Tier, visibly dividing standard application code and custom code across the APPL_TOP and COMMON_TOP directories. At the same time, the Database tier leverages editioned schemas, separating custom data models and logic (Custom Code, Custom Schemas) from core Oracle-supplied application schemas.
This architectural flexibility enables organizations to craft sophisticated extensions without directly altering core Oracle code. However, this separation allows customizations, especially poorly documented or loosely governed ones, to evade Oracle’s native security layers and compliance controls.
Where the Risks Hide
Application Tier (APPL_TOP & COMMON_TOP):
- Custom code exists alongside Oracle’s standard code and must be “synced” across environments.
- Suppose customizations are not adequately governed or reviewed. In that case, they can introduce vulnerable code (e.g., susceptible to SQL injection or excessive privileges) outside the scope of Oracle’s standard update and security review mechanisms.
- These customizations can include web logic modifications, developer tools, or even custom web listeners, each a potential attack surface if not reviewed for security holes.
Database Tier (Editioned Schemas):
- Custom code within the application and dedicated custom schemas can bypass built-in Oracle controls.
- Audit trails, access controls, and role-based protections typically apply to Oracle-delivered objects. Still, unless explicitly configured, custom tables, views, or PL/SQL code may not benefit from these defences.
- Custom Data Models are especially risky if they process or store sensitive data without standardized security measures like encryption, logging, or auditing.
Compliance Blind Spots
Because customizations exist at every layer and are often treated as distinct from Oracle-delivered assets, they can easily fall outside the purview of automated compliance checks. For example:
- Audit trails may not include custom transaction flows.
- Separation of duties enforced in standard modules can be negated by bespoke custom logic.
- Patch management processes may overlook legacy or undocumented customizations, leaving vulnerabilities unaddressed.
The image serves as a crucial reminder: Oracle EBS customizations create parallel technology tracks, one supported by Oracle controls, and another (custom code) that must be secured and audited independently. Regular, rigorous review of all customizations across application and database layers is the only way to close hidden vulnerabilities, avoid compliance failures, and protect the integrity of your business-critical Oracle EBS environment.
Establish Technical Debt Metrics and Monitoring
Quantify technical debt using measurable indicators that resonate with business stakeholders. Key metrics include:
- Technical Debt Ratio (TDR): Cost to fix debt relative to development cost
- Code Churn Rate: Frequency of changes to customized components
- Defect Ratio: Number of bugs relative to custom code volume
- Change Failure Rate: Percentage of customization deployments requiring immediate fixes
Implement “Clean Code” Development Standards
Establish and enforce development standards that minimize future technical debt. Requirements should include:
- Mandatory use of Oracle-supported APIs for all data access
- Custom code isolation in separate schemas (never modify the APPS schema directly)
- Comprehensive documentation for all customizations
- Automated testing coverage for custom components
- Version control for all custom development assets
Plan Strategic Debt Reduction
Allocate dedicated capacity for technical debt reduction within regular development cycles. Effective strategies include:
- Reserve 10-20% of each sprint for debt reduction activities
- Prioritize debt reduction based on business impact and remediation complexity
- Focus on customizations that affect frequently-used business processes
- Replace custom functionality with standard Oracle capabilities when possible
Building the Business Case for Technical Debt Reduction

CTOs must translate technical challenges into business language that resonates with executive leadership. Frame technical debt reduction as:
- Risk Mitigation: Reduced security vulnerabilities and compliance gaps
- Cost Optimization: Lower maintenance costs and improved operational efficiency
- Business Agility: Faster implementation of new features and business processes
- Competitive Advantage: Improved system performance and user experience
Model the ROI of debt reduction using concrete financial projections. Include costs of inaction, such as delayed upgrades, security incident response, and lost productivity due to system instability.
The Path Forward: Proactive Technical Debt Management
Oracle EBS customizations will continue to be necessary to meet unique business requirements. However, organizations must adopt a proactive approach to technical debt management, treating customizations as financial investments requiring ongoing maintenance and eventual retirement.
Success requires treating technical debt as a measurable business liability rather than an abstract technical concept. By implementing systematic audits, establishing clear development standards, and allocating dedicated resources for debt reduction, organizations can maintain the flexibility customizations provide while avoiding the hidden risks that threaten long-term system sustainability.
The organizations that thrive in the evolving Oracle landscape will recognize technical debt as a strategic concern requiring C-level attention and systematic management. The cost of inaction, measured in security vulnerabilities, compliance failures, and lost competitive advantage, far exceeds the investment required for proactive debt management.
For technology leaders, the message is clear: Oracle EBS customizations are not just code, they’re business assets that require active management to deliver lasting value. The time to act is before technical debt transforms from a manageable challenge into an existential threat to your organization’s technological foundation. Talk to our Oracle EBS experts to build an upgrade roadmap tailored to your enterprise set up; contact us at hello@appstekcorp.com.

About The Author
Rahul Sudeep, Senior Director of Marketing at AppsTek Corp, is a results-driven, AI-first B2B marketing leader with 15 years of experience scaling global enterprise SaaS companies. His expertise, honed at IIM-K, spans architecting high-impact go-to-market strategies, driving new market identification and positioning, and embedding Generative AI, LLMs, and predictive analytics into the core marketing function. Rahul unifies Technology, Sales, and Support teams around a single strategic hub, while also managing key Partner and Investor Relations. He leverages AI-driven insights to craft powerful brand narratives and hyper-personalized demand generation campaigns that drive measurable revenue growth and deepen customer engagement.