Questioning is one of the biggest secrets of human evolution. Every ancient or modern development can be traced back to a question / pain experienced, at a given point of time by persons / societies. It is essential to be curious, challenge the status quo to bring the next level of perfection and solution for any given impediment. Modern age distributed / Internet enabled applications require so much sophistication not just to serve the purpose but also must be immensely secure considering the threat landscape.
Building secure applications must begin simultaneously with product conception, much earlier than writing the first line of code, but along with the requirements elicitation and continue through the entire lifecycle. It is essential to bake security all along to build a system that protects the underlying sensitive data / information and environments.
This is an attempt to adopt the popular questioning method 5W1H or the method of the Five Ws. 5W1H is an acronym in which every letter corresponds to a question: what, who, where, when, how, and why. We can systematically question any given scenario to identify the underlying facts, challenges, and roles to arrive at a workable modal.
Consider the below table, eliciting the 5Ws and 1H for every representative phase of Secure Software Development Life Cycle (SSLDC). Not waterfall as it might look at first glance. All modern development methodologies will have incremental / phased engineering activities, resulting in a successful system development to deployment and beyond.
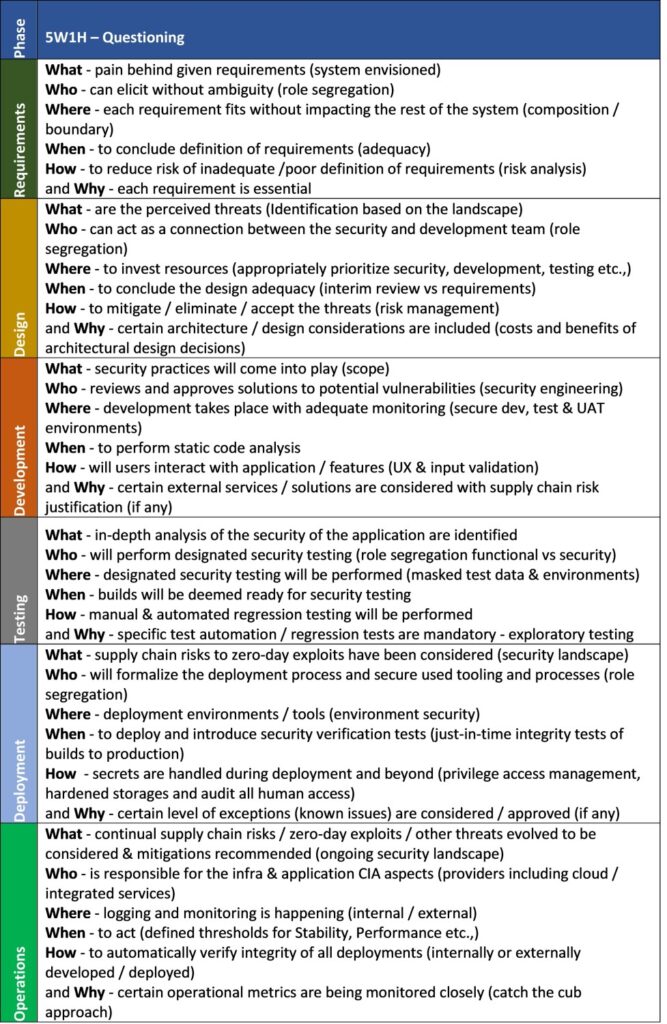
5W1H Approach for Secure Software Development Life Cycle (SSLDC)
Building secure applications with clean coding practices is a culture to build, it requires focused efforts from every stakeholder and serves a bigger purpose – “enhanced application security.”
Do share your thoughts for us to mature these ideas and engage in continual learning. This article is an outcome of years of experience in system engineering and other management frameworks implementations and readings online / offline.